One of the important areas you need to master when analyzing memory dumps is to recognize patterns that are normal and not normal. You can only come to those conclusions after looking at many, many, many, many memory dumps and either remembering or taking notes on how a process looks when all is ok, so that when, what you see is having a different pattern, then you can drill deeper in that area looking for the cause of the issue for which you took the memory dump for in the first place. One such scenario is knowing what NULL, True, False, empty strings look like.
Create a simple Console application with this code:
namespace values
{
class Program
{
static bool boolTrue = true;
static bool boolFalse = false;
static bool? nullableBoolTrue = true;
static bool? nullableBoolFalse = false;
static bool? nullableBoolNull = null;
static byte byteValue = 123;
static char charValue = 'X';
static decimal decimalValue = 12.34m;
static float floatValue = 12.34f;
static string stringEmpty = "";
static string stringValue = "abc123";
static string stringNull = null;
static int intValue = 123;
static int? nullableIntNull = null;
static int? nullableIntValue = 123;
static SimpleClass referenceNull = null;
static SimpleClass referenceNotNull = new SimpleClass();
static Line structValue = new Line(1, 1);
static List<SimpleClass> populatedList = new List<SimpleClass>() { new SimpleClass { simpleProperty = 100 } };
static void Main(string[] args)
{
Program p = new Program();
WriteLine("Wait for WinDbg break in.");
ReadKey();
}
public struct Line
{
public int x, y;
public Line(int p1, int p2)
{
x = p1;
y = p2;
}
}
public class SimpleClass
{
public int simpleProperty { get; set; }
}
}
}
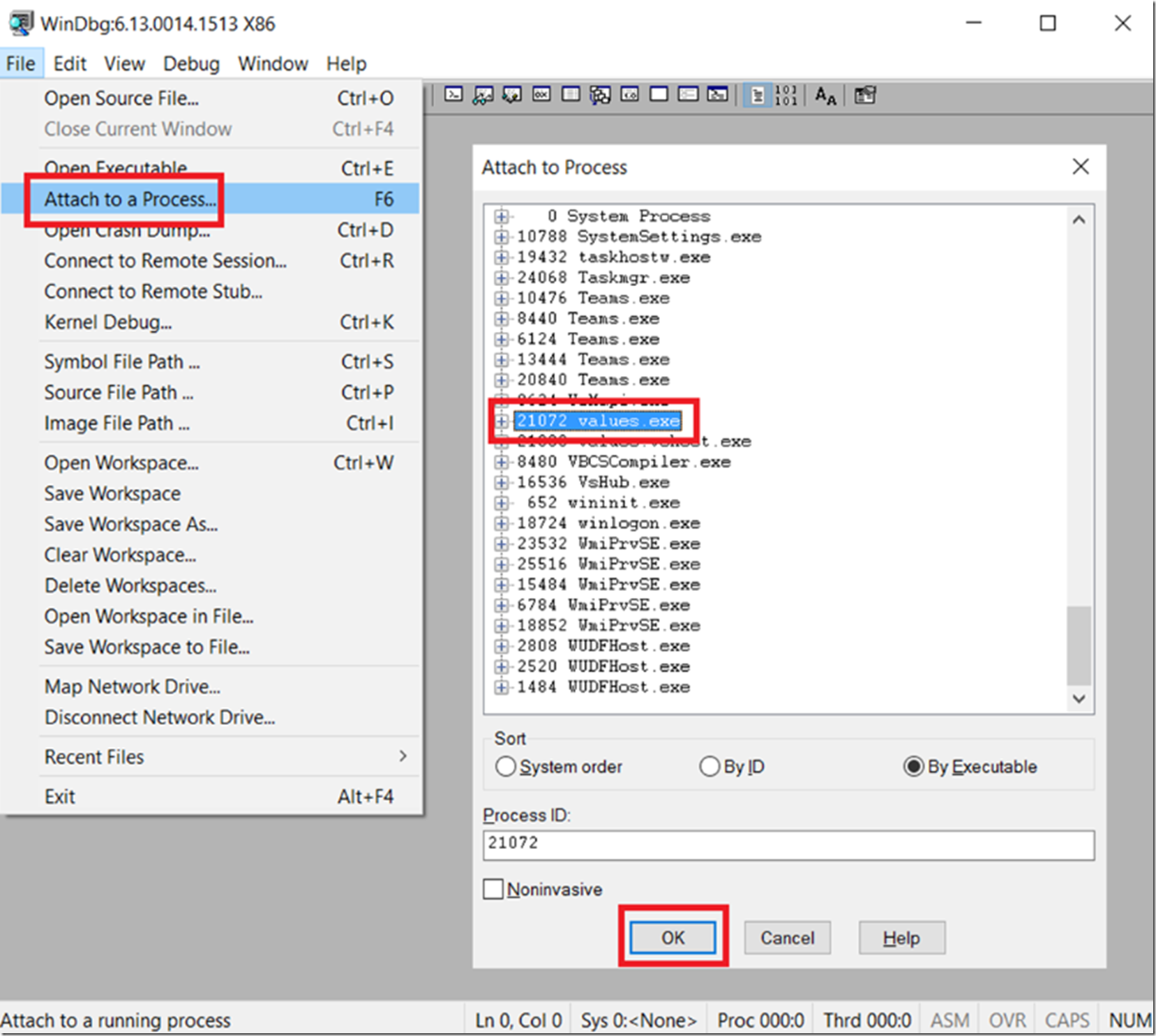
Run the code and then open WinDbg, in this case the 32 bit version and attach WinDbg to the process, as shown in Figure 1.
Figure 1, attach WinDbg to a process
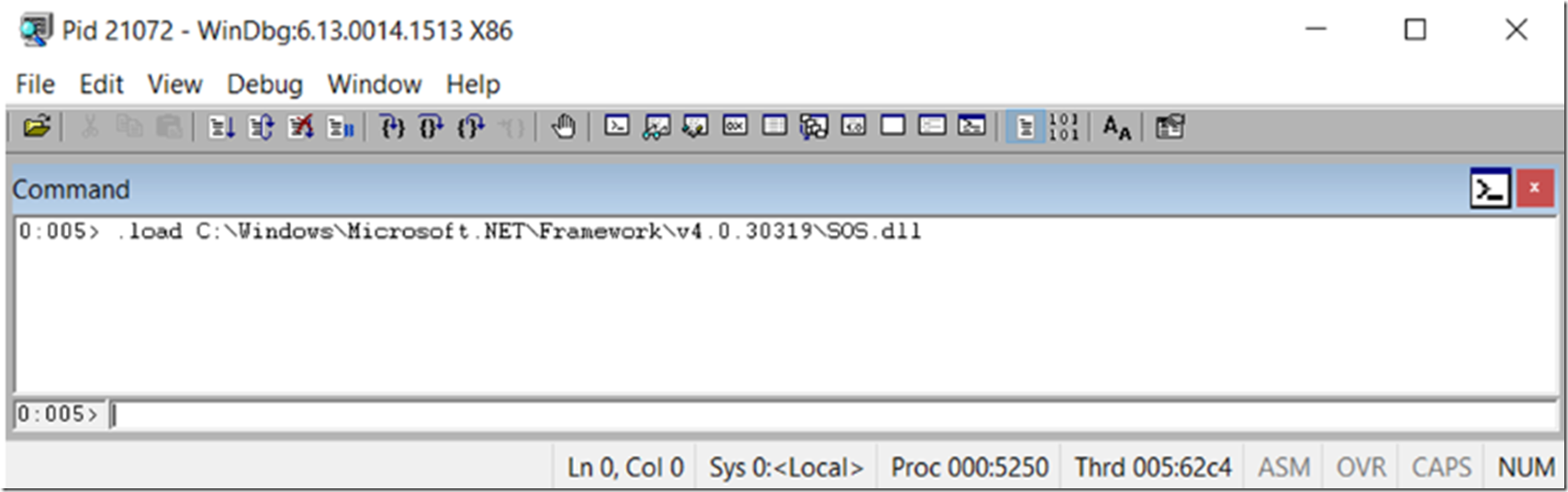
Load the SOS.dll debug extension, as shown in Figure 2.
Figure 2, load SOS debug extension in WinDbg to debug or analyze a proces
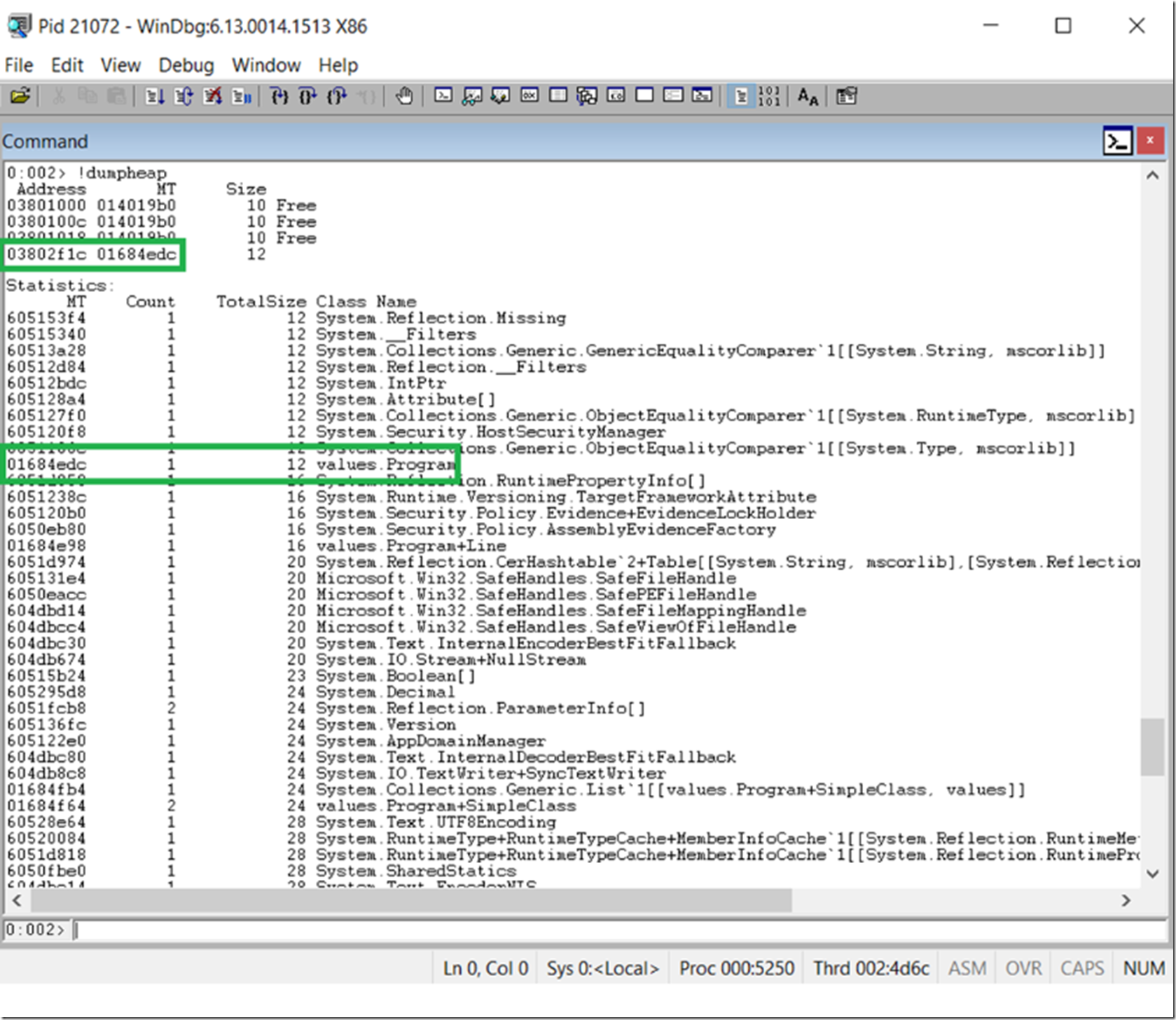
Dump out the heap using !SOS.Dumpheap and find the Address of the values.Program, as seen in Figure 3.
Figure 3, dump the heap in WinDbg to find objects stored in memory of a process
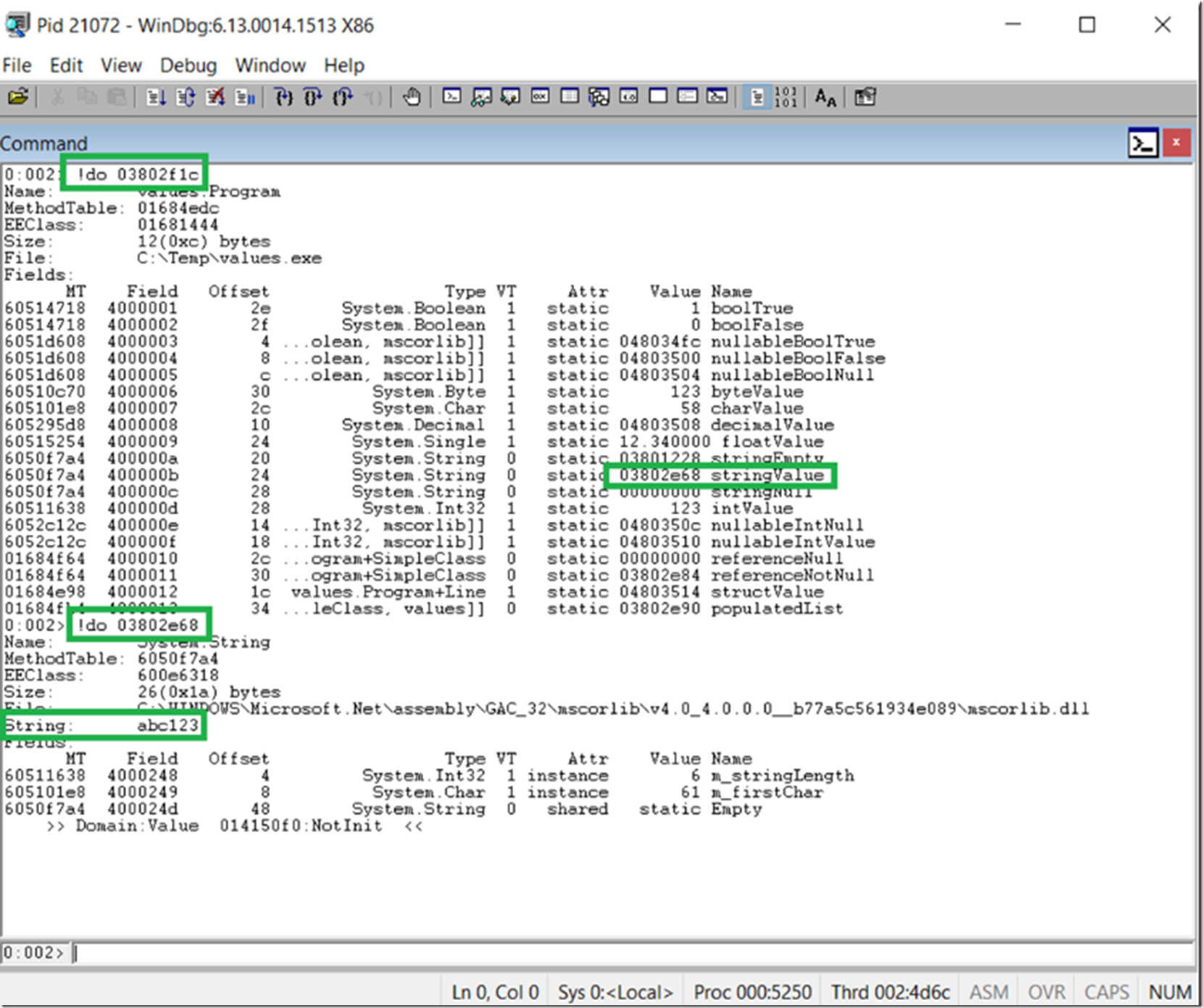
Dump the object using the !SOS.Dumpobject method and its address found previously. See Figure 4.
Figure 4, view the values of class objects within a process
Notice that a bool set to True is 1 and False is 0, just like you have been taught, notice the the StringNull is 00000000 and that the stringValue has a memory address of 03802e68. Dump that out using !do and you will see its value of abc123, just like it is set in the code.
0:002> !do 03802f1c
Name: values.Program
MethodTable: 01684edc
EEClass: 01681444
Size: 12(0xc) bytes
File: C:\Temp\values.exe
Fields:
MT Field Offset Type VT Attr Value Name
60514718 4000001 2e System.Boolean 1 static 1 boolTrue
60514718 4000002 2f System.Boolean 1 static 0 boolFalse
6051d608 4000003 4 …olean, mscorlib]] 1 static 048034fc nullableBoolTrue
6051d608 4000004 8 …olean, mscorlib]] 1 static 04803500 nullableBoolFalse
6051d608 4000005 c …olean, mscorlib]] 1 static 04803504 nullableBoolNull
60510c70 4000006 30 System.Byte 1 static 123 byteValue
605101e8 4000007 2c System.Char 1 static 58 charValue
605295d8 4000008 10 System.Decimal 1 static 04803508 decimalValue
60515254 4000009 24 System.Single 1 static 12.340000 floatValue
6050f7a4 400000a 20 System.String 0 static 03801228 stringEmpty
6050f7a4 400000b 24 System.String 0 static 03802e68 stringValue
6050f7a4 400000c 28 System.String 0 static 00000000 stringNull
60511638 400000d 28 System.Int32 1 static 123 intValue
6052c12c 400000e 14 …Int32, mscorlib]] 1 static 0480350c nullableIntNull
6052c12c 400000f 18 …Int32, mscorlib]] 1 static 04803510 nullableIntValue
01684f64 4000010 2c …ogram+SimpleClass 0 static 00000000 referenceNull
01684f64 4000011 30 …ogram+SimpleClass 0 static 03802e84 referenceNotNull
01684e98 4000012 1c values.Program+Line 1 static 04803514 structValue
01684fb4 4000013 34 …leClass, values]] 0 static 03802e90 populatedList
0:002> !do 03802e68
Name: System.String
MethodTable: 6050f7a4
EEClass: 600e6318
Size: 26(0x1a) bytes
File: C:\WINDOWS\Microsoft.Net\assembly\GAC_32\mscorlib\v4.0_4.0.0.0__b77a5c561934e089\mscorlib.dll
String: abc123
Fields:
MT Field Offset Type VT Attr Value Name
60511638 4000248 4 System.Int32 1 instance 6 m_stringLength
605101e8 4000249 8 System.Char 1 instance 61 m_firstChar
6050f7a4 400024d 48 System.String 0 shared static Empty
>> Domain:Value 014150f0:NotInit <<