This happened to me way back in 2011. I am migrating all my blogs and articles to this site and am adding it here. This shouldn’t happen anymore if you use an ORM like Entity Frame Work or NHibernate.
A few weeks ago I had to fend off a hacker. Some of the database statements I created for another website were susceptible to SQL injection. This means I created the statements like this.
[sourcecode language="csharp" padlinenumbers="true" autolinks="false" gutter="false" toolbar="false"] string query = "select name, email, comment " + "from blogs where postdate >= " + DateTime.Now.AddDays(-15); [/sourcecode]
This is not good because a hacker can place something like:
[sourcecode language="csharp" padlinenumbers="true" autolinks="false" gutter="false" toolbar="false"] "’ or 1=1 " [/sourcecode]
Into the query value and get all the data versus avoiding the constraint. This is an extra problem with login and password functionality. If you have a query which is formatted like the above which checks user id and password using a simple where clause, then your system is open to the simplest attack known to man.
But anyway, I fixed the problem, I won’t share what I did because it could open other holes so, just know that I am watching, on the ball and the problem is fixed. This is NOT a challenge, leave my website alone.
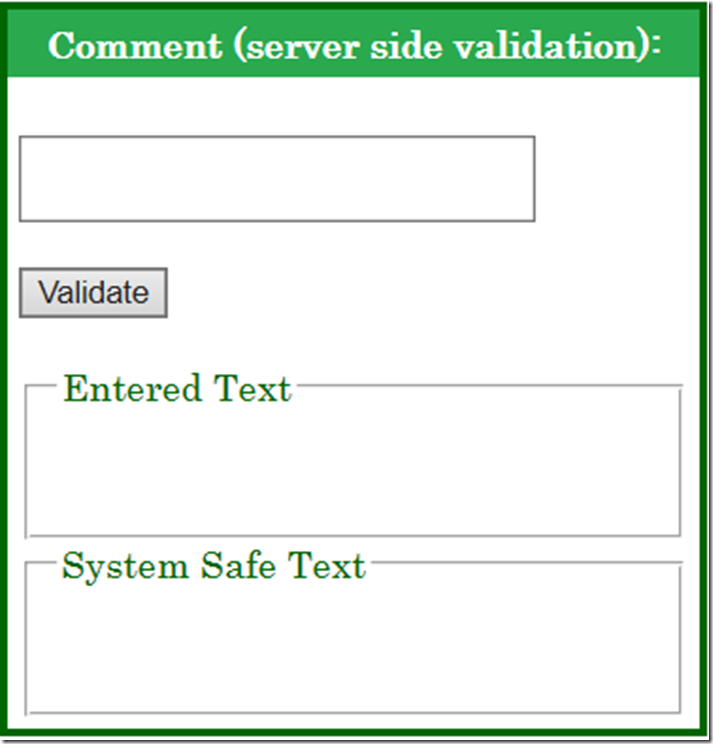
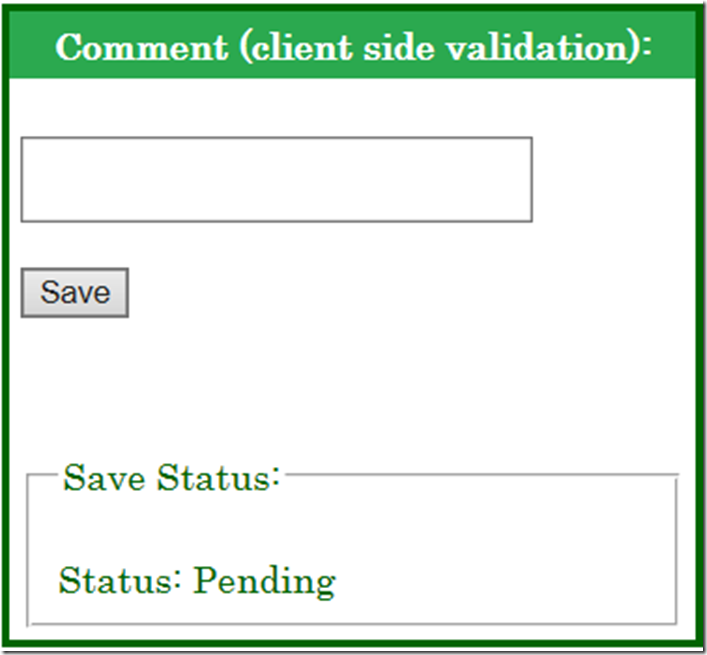
And recently another attack happened on this website. I have a feedback form with limited validation, so really anyone can put anything into the fields and submit. Others will see the entered data. What someone or people have done was put other web addresses or JavaScript into the comment form which either redirected or presented the person with some advertisement. So, I fixed that one using the RegularExpressionValidator server control. You can still put in web addresses however no links or special characters are allowed.
I still enjoy getting comments, please continue and keep learning…
The tools below represent some of the restrictions I have placed on the website sue to hackers.
Download the source