When you run an ASP.NET application on multiple instances of an App Service Plan (ASP) you do not need to worry about machineKeys as the App Service Platform will use the same one across all your instances and therefore will not need to make any changes to your application.
I found this sample code and deployed it to an Azure App Service Web App running 3 instances:
HttpCookie protectCookie = Request.Cookies["MCENCRYPT"];
if (protectCookie == null)
{
var protectedText = MachineKey.Protect(System.Text.Encoding.ASCII.GetBytes("EncryptThisText"), "ciphertext");
var unprotectedText = Encoding.ASCII.GetString(MachineKey.Unprotect(protectedText, "ciphertext"));
protectCookie = new HttpCookie("MCENCRYPT");
protectCookie.Value = Convert.ToBase64String(protectedText);
Response.Cookies.Add(protectCookie);
labelMachineKey.Text = $"Proctected TXT-> {Convert.ToBase64String(protectedText)} : " +
$"Unprotected TXT -> {unprotectedText} : ProcessID is {Process.GetCurrentProcess().Id} : " +
$"Machine name is {Environment.MachineName}";
}
else
{
var unprotectedText = System.Text.Encoding.ASCII
.GetString(MachineKey.Unprotect(Convert.FromBase64String(protectCookie.Value), "ciphertext"));
labelMachineKey.Text = $"Unprotected TXT-> {unprotectedText} : " +
$"ProcessID is {Process.GetCurrentProcess().Id} : Machine name is {Environment.MachineName}";
}
The above code looks for a cookie named MCENCRYPT and if it is not found then it creates one and encrypts it using the machine key. Then it writes out the encrypted/protected text, the unprotected text, the W3WP process ID and the Azure App Service machine name which responded to the request.
If a cookie name MCENCRYPT does exist, then it will use the machine key to decrypt the cookie and display it along with the W3WP process ID and the name of the machine that responded to the request. In this example I have 3 instances, which constitute 3 different machines.
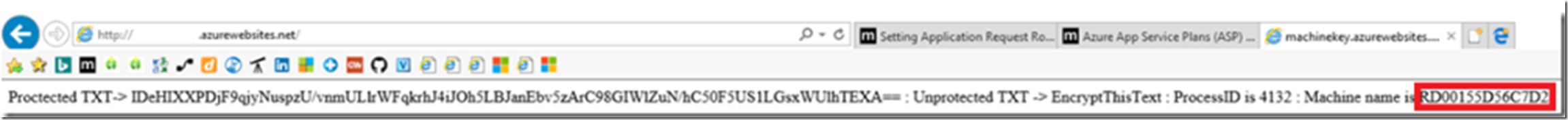
Notice in Figure 1, that as I had no cookie on my client machine that the code encrypted one and displayed the expected information into the browser.
Figure 1, machine key on multiple Azure App Service Web App instances
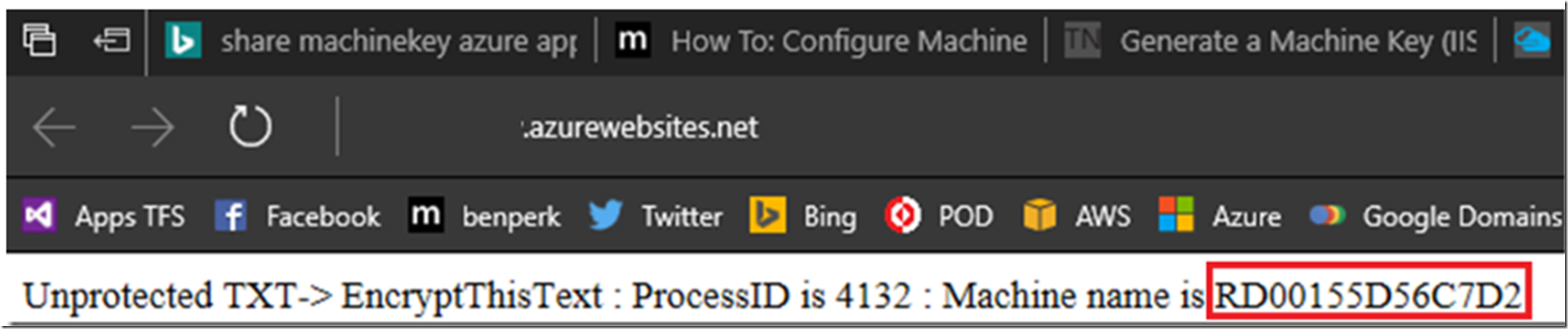
In figure 2, you see that the cookie was found and responded to from the same server, in that case, sure, we would expect the machine key to be the same because the request was responded to by the same machine.
If you are testing this you will have more luck in getting your request sent to other machines in your web farm is you disable ARR Affinity as I discuss here “Setting Application Request Routing – ARR Affinity for your Azure App Service”
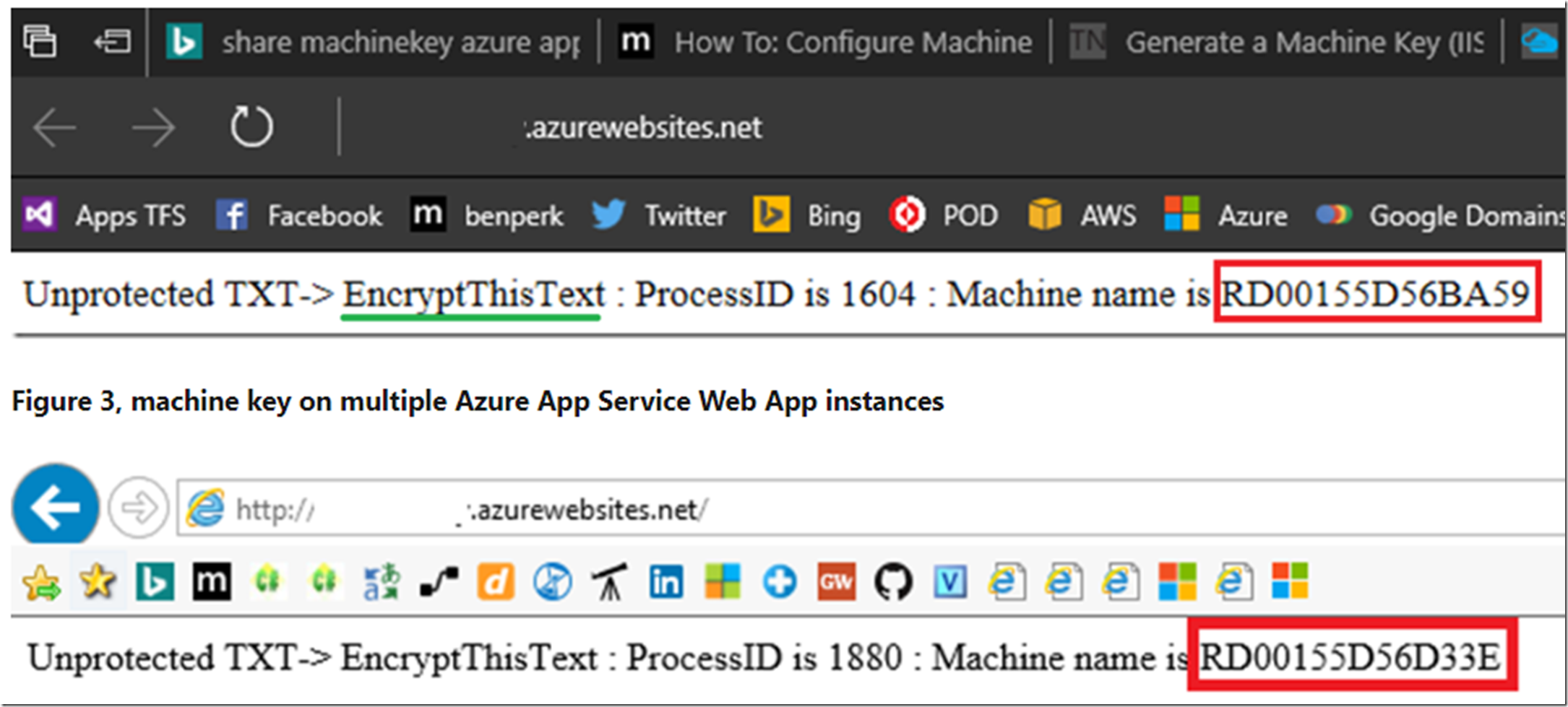
So, to prove that the same machine key was used I hit refresh until my request was responded to by the other 2 machines in my web farm, ASP instances. Notice the following:
- The machine name is different in both Figure 3 and Figure 4 when compared to Figure 1 and Figure 2.
- The Unprotected TXT has been decrypted successfully which means it used the same machine key to decrypt as was used to encrypt
Figure 4, machine key on multiple Azure App Service Web App instances
ASP.NET Core
This above is for ASP.NET applications, there are some new features in ASP.NET Core which would be a more preferred method for example:
- Getting Started with the Data Protection APIs
- Key management and lifetime
- Azure Web App and ASP.NET 5 Data Protection keys