I wrote an article here that describes how to connect to a Web App from IIS manager. If you cannot do that, read down at the bottom of the article where I show the configuration you can add to the web.config manually.
Here is a document that discusses this feature in more detail.
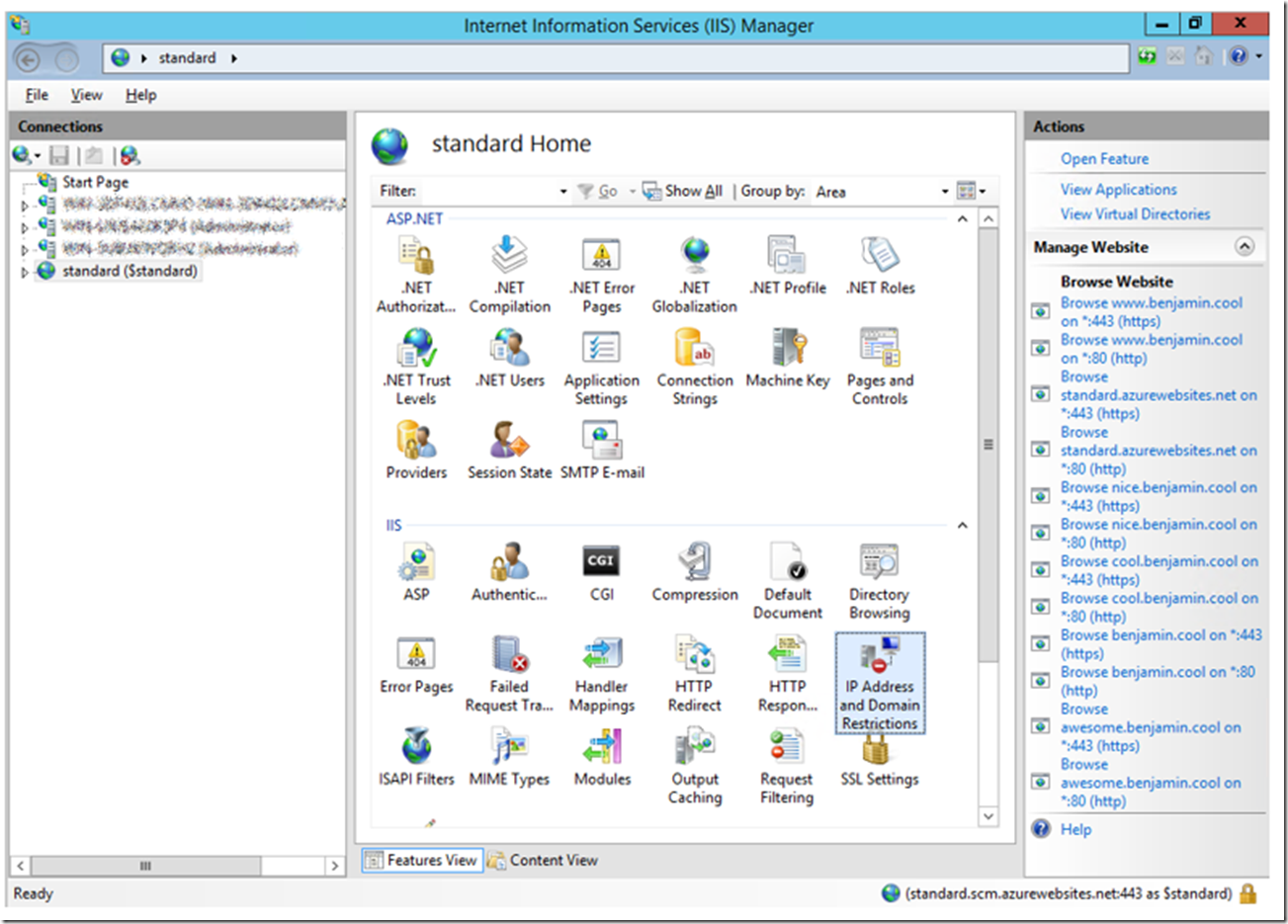
Once you have configured the App Service with the IIS Management console, you will see the IP Address and Domain Restrictions icon, similar to that in Figure 1.
Figure 1, setup IP security restrictions for an Azure App Service (Web App, Mobile App, API App, Logic App)
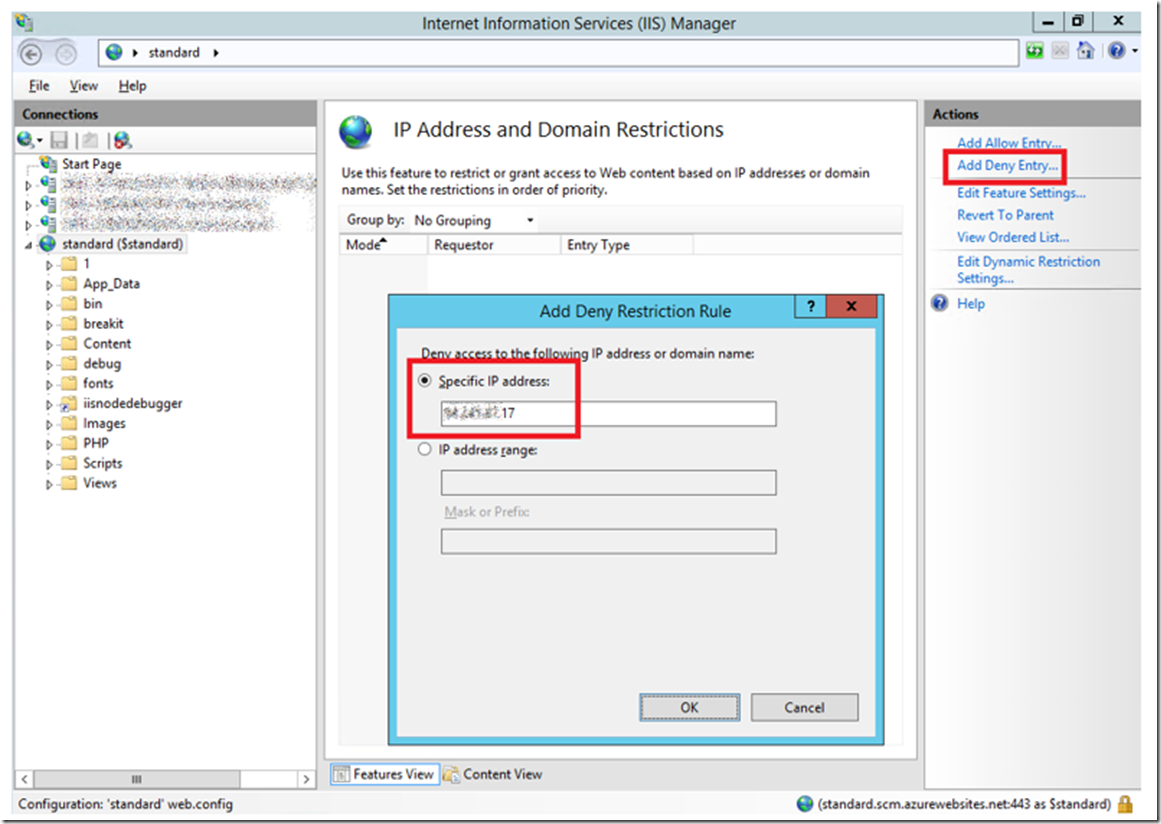
As a test I am going to Deny access to my IP address for this Web App. I found my IP address here. With that information I added it to the Deny Restriction Rule, as shown in Figure 2.
Figure 2, adding an IP deny restriction rule to an Azure App Service
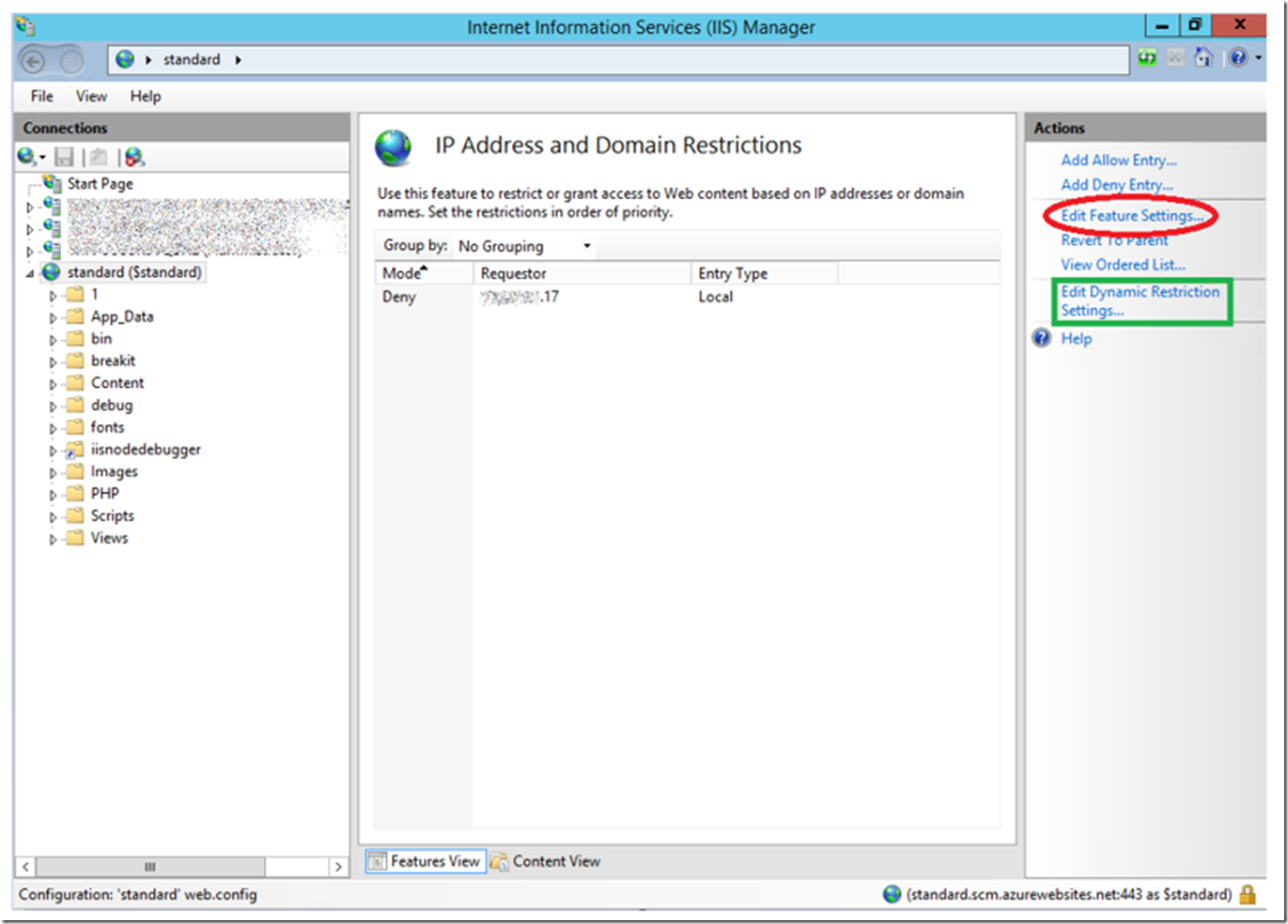
Clicked OK which added the Deny rule to the configuration. You should see the rule added to the feature pane similar to that in Figure 3.
Figure 3, adding an IP deny restriction rule to an Azure App Service
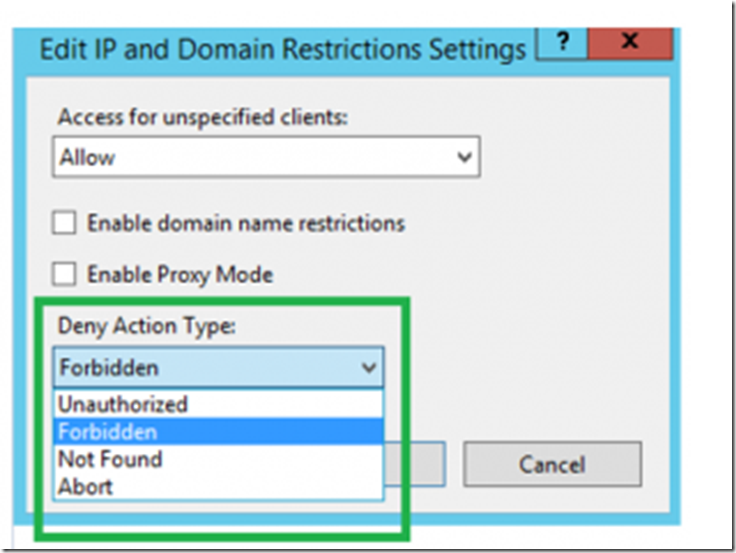
NOTE: I did see a lag between the time I created this rule and the time it started acting as I expected. To make it effective quickly, I scaled up or down so my VM is recreated and it work immediately after that. If you select Edit Feature Settings as shown in Figure 3, you can control the response (Deny Action Type) IIS sends to the client, see Figure 4.
Figure 4, adding an IP deny action type an Azure App Service
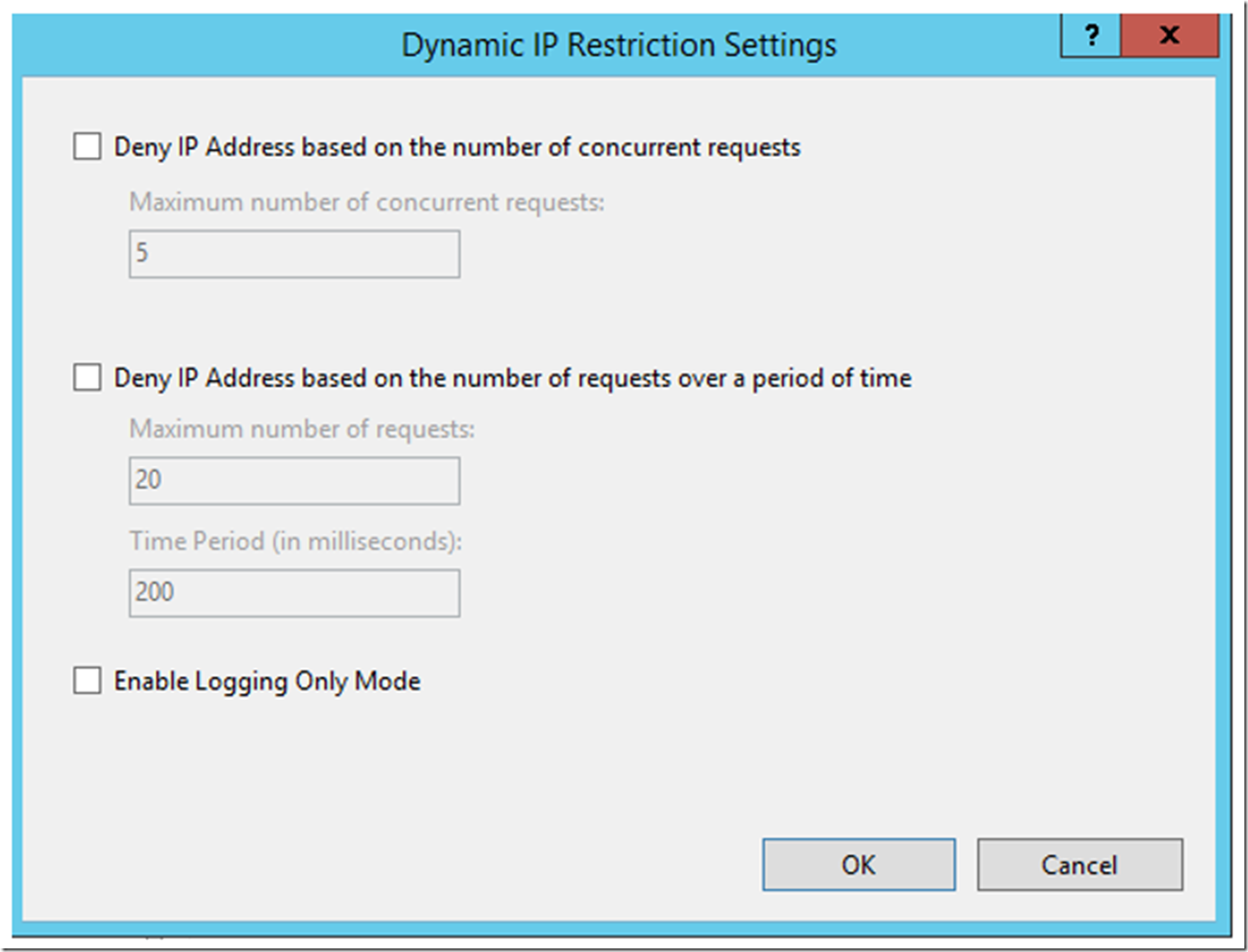
Where Unauthorized returns a 401, Forbidden a 403, Not Found a 404 and Abort, I received a 502. You can also configure Dynamic IP Restrictions by clicking on the Edit Dynamic IP Restrictions, also shown in Figure 3 previously. Clicking on that link renders this window, Figure 5, for making the configurations.
Figure 5, adding an IP deny action type an Azure App Service
You can read about Dynamic IP Restrictions here for the details. Quoted from this page „The Dynamic IP Restrictions Extension for IIS provides IT Professionals and Hosters a configurable module that helps mitigate or block Denial of Service Attacks or cracking of passwords through Brute-force by temporarily blocking Internet Protocol (IP) addresses of HTTP clients who follow a pattern that could be conducive to one of such attacks.“